Series on Information Security - Weekly -Part 13
The below mentioned concepts gives insight into how to identify the services and their version running on the servers so that it will help in finding the vulnerabilities associated with a particular version of service and can be exploited.
Service identification
The port are mapped to service that are offered by the system. If you want to find out the services that run on the systems and their associated port numbers , here is a way to find out.
Microsoft Windows : "c:\windows\system32\drivers\etc\services"
*NIX systems: "/etc/services"
One can use simple utilities like telnet that is generally available with Windows as well as *nix operating system to find out what is the application/service is running on a particular pot. As a system administrator it is a bare minimum requirement to have telnet utility available (which generally is) to remotely diagnose if the a particular service is running on a machine. I will demonstrate here an example that shows how telnet can be used as a diagnostic tool for system administrator and the same can be used by attacker to collect more information about the services running on a particular system.
Here is an example,
Use the following command to see if web server is running on remote host,
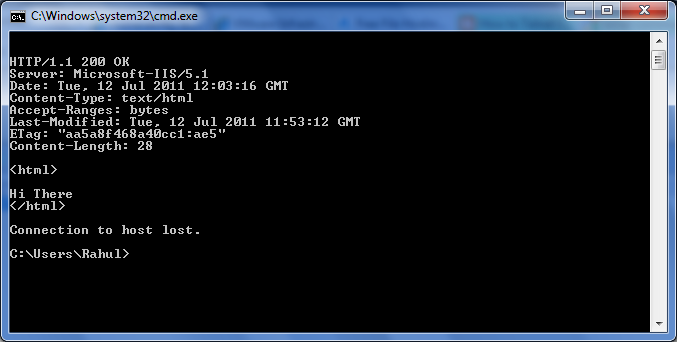
C:\> telnet 192.168.1.8 80
GET default.html HTTP/1.0
If you get following response , it indicates that the web server is running on the remote machine with the ip address 192.168.1.18
4. Banner grabbing
Though the above example shows the port/service scanning method, if you observe carefully it also shows that it supports HTTP 1.1 protocol and in fact the server software that is running on the machine is Microsoft - IIS 5.1. This process of acquiring specific information about the OS and application/service version is known as Banner grabbing.
I will mention another example of banner grabbing. Here I have used again the same telnet client utility to gather more information about service running on port 25. Here you can make out the information like the service running is SMTP. The application that is running is Microsoft ESMTP , version 6.0.2600.5949 .
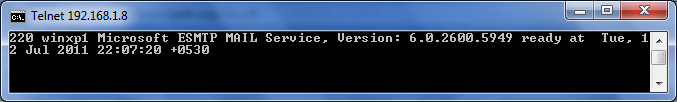
Once the attacker have the above mentioned information available with him , he just needs to find out exploits associated with the particular version of the service .
OS Fingerprinting: It is a process of gathering information and utilizing the gathered information of the target to find out the OS on the system.
Here is the command that can be used with nmap utility to do OS fingerprinting,
c:\> nmap -F -sT -O 192.168.1.8
and following is the output,
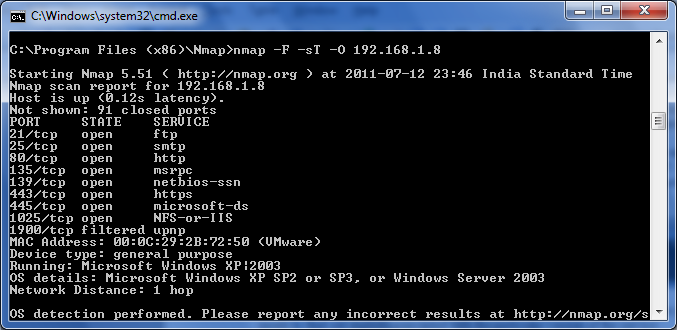
Please observe the bottom of the screen, the Nmap utility has detected the probable OS system i.e. Microsoft XP or 2003.
Another utility to do finger printing is Xprobe2. As we know that Nmap uses TCP packets, Xprobe2 uses icmp packet to do OS fingerprinting.
