Series on Information Security - Weekly -Part 11
As a part of reconnaissance , one can use the the methods mentioned below.
Websites that can be used to collect information is for APNIC , ARIN ,
<a href="https://www.dnsstuff.com" target="_blank" rel="nofollow noopener noreferrer">Software Reviews, Opinions, and Tips - DNSstuff</a>,
#-Link-Snipped-#,
<a href="https://www.lacnic.net" target="_blank" rel="nofollow noopener noreferrer">Registro de Direcciones IP en LAC | LACNIC</a> etc.
Similarly the few of the tools that can be used for reconnaissance purpose are,
a) Nmap (#-Link-Snipped-#) : IP and port scanning tool
b) NSlookup,dig : A tool for discovering IP information on DNS names
Tools used for scanning
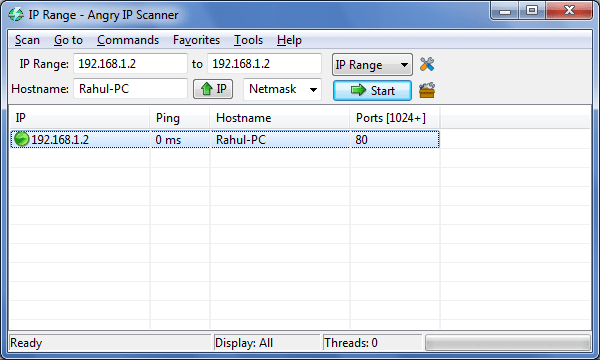
Angry IP Scanner : A fast and small IP scanner. It pings each IP address to check whether it is alive. Then, optionally, it resolves host names and tries to connect as specified in the Options dialog box TCP port. The advantage of using Angry IP Scanner is the feature that allows to store the results in csv and xml format. The tool is available at #-Link-Snipped-#.
Here is a sample screen shot for Angry IP scanner.
This is again pre-attack phase. Remember we have already collected some basic information in the reconnaissance attack. This information can be used further for scanning attacks. Here we can collect information like is there any modems available , what are the ports that are available, can we exploit the ports or service, version of application , version of OS , vulnerability associated with particular version of application , service or operating system. At this stage the attack is becoming more of an active attack rather than passive attack. Here the probability of getting detected is more as compared to the previous stage. There are many tools that are available for scanning that includes commercial as well as open source.
There are numerous Scanning Techniques that can be used for different types of scanning. Here are the scanning techniques under different scenarios.
i) Port scanning,
ii) Wardialing,
iii) wardriving
iv) vulnerability scanning,
v) Network mapping
In the next section we will dive into greater details of the scanning scenarios.
Websites that can be used to collect information is for APNIC , ARIN ,
<a href="https://www.dnsstuff.com" target="_blank" rel="nofollow noopener noreferrer">Software Reviews, Opinions, and Tips - DNSstuff</a>,
#-Link-Snipped-#,
<a href="https://www.lacnic.net" target="_blank" rel="nofollow noopener noreferrer">Registro de Direcciones IP en LAC | LACNIC</a> etc.
Similarly the few of the tools that can be used for reconnaissance purpose are,
a) Nmap (#-Link-Snipped-#) : IP and port scanning tool
b) NSlookup,dig : A tool for discovering IP information on DNS names
Tools used for scanning
Angry IP Scanner : A fast and small IP scanner. It pings each IP address to check whether it is alive. Then, optionally, it resolves host names and tries to connect as specified in the Options dialog box TCP port. The advantage of using Angry IP Scanner is the feature that allows to store the results in csv and xml format. The tool is available at #-Link-Snipped-#.
Here is a sample screen shot for Angry IP scanner.

This is again pre-attack phase. Remember we have already collected some basic information in the reconnaissance attack. This information can be used further for scanning attacks. Here we can collect information like is there any modems available , what are the ports that are available, can we exploit the ports or service, version of application , version of OS , vulnerability associated with particular version of application , service or operating system. At this stage the attack is becoming more of an active attack rather than passive attack. Here the probability of getting detected is more as compared to the previous stage. There are many tools that are available for scanning that includes commercial as well as open source.
There are numerous Scanning Techniques that can be used for different types of scanning. Here are the scanning techniques under different scenarios.
i) Port scanning,
ii) Wardialing,
iii) wardriving
iv) vulnerability scanning,
v) Network mapping
In the next section we will dive into greater details of the scanning scenarios.
0
