Protecting Your Google Nexus Phone From Flash SMS Based DoS Attack
Google Nexus owners across the world are concerned regarding the well-being of their beloved smartphone after learning about Flash SMS based denial-of-service attacks that can affect the performance of several flagship Android smartphones which run Android 4.x firmware. The issue was discovered by Bogdan Alecu who says that if an attacker sends a large number of Class 0 SMS or Flash SMS and if the receiver does not discard them in time then the phone malfunctions in one of the following ways:
(a) The phone reboots and after the reboot if the SIM is protected by a PIN then it would not be able to connect to the network.
(b) The phone loses connection to the cellular network temporarily.
(c) The messaging app crashes causing a system restart.

The scariest part of this attack as mentioned on #-Link-Snipped-# is that threat prone devices like Google Galaxy Nexus, LG Nexus 4 and LG Nexus 5 do not have audio notifications for Class 0 SMS/Flash SMS so the victim has no way of knowing when he/she is being attacked unless they are looking directly at the screen. Google representatives say that they are looking into the problem but did not reveal any tentative date for a bug fix.
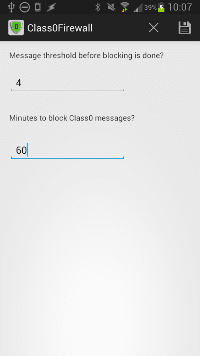
If you want immediate solution though, folks over at #-Link-Snipped-# have stumbled on a free app developed by Silent Services that can protect you from this exploit. The #-Link-Snipped-# is based on the observations made by Alecu. According to Alecu, the problem occurs when around thirty Flash SMS are received by the Android smartphone, so the app helps you set threshold values and the block duration for such messages. The first field in the app is meant for setting the maximum number of messages per minute and the second field is used to alter the time limit. The app blocks the stream of Class 0 messages and safeguards your Nexus smartphone. The app will be getting additional features in its next version which will release soon.


(a) The phone reboots and after the reboot if the SIM is protected by a PIN then it would not be able to connect to the network.
(b) The phone loses connection to the cellular network temporarily.
(c) The messaging app crashes causing a system restart.

The scariest part of this attack as mentioned on #-Link-Snipped-# is that threat prone devices like Google Galaxy Nexus, LG Nexus 4 and LG Nexus 5 do not have audio notifications for Class 0 SMS/Flash SMS so the victim has no way of knowing when he/she is being attacked unless they are looking directly at the screen. Google representatives say that they are looking into the problem but did not reveal any tentative date for a bug fix.
If you want immediate solution though, folks over at #-Link-Snipped-# have stumbled on a free app developed by Silent Services that can protect you from this exploit. The #-Link-Snipped-# is based on the observations made by Alecu. According to Alecu, the problem occurs when around thirty Flash SMS are received by the Android smartphone, so the app helps you set threshold values and the block duration for such messages. The first field in the app is meant for setting the maximum number of messages per minute and the second field is used to alter the time limit. The app blocks the stream of Class 0 messages and safeguards your Nexus smartphone. The app will be getting additional features in its next version which will release soon.



0
