Over 3 Lakh Routers Around The World Have Been Compromised: A Team Cymru Finding
A global internet security research firm has made a startling discovery. According #-Link-Snipped-# over 3, 00,000 small office and home routers have been compromised by unknown attackers. In the report titled “Growing Exploitation of Small Office Routers Creating Serious Risks†Team Cymru (pronounced "kum-reeâ€) have found out that routers from various countries in Europe and Asia have been compromised by what they term as a SOHO pharming (SOHO stands for small office and home office routers). A majority of these compromised routers are from Vietnam, India, Italy and Thailand. All of affected devices had their DNS settings changed from their ISP’s default to two specific IP addresses hailing from South London (5.45.75.11 and 5.45.75.36). The attack was carried out in two ways as follows:
- In the first case, the attackers used a malicious code to target routers which had graphical user interfaces that were accessible from the Internet and then they carried out simple brute force log-on attempts to get access to the router’s configuration.
- Secondly, they targeted routers which were vulnerable to the “ROM-0†attack. The routers which ran ZyXEL’s ZynOS allowed attackers to download the configuration file from an unsecured URL. This configuration file (ROM-0) could then be used to change the DNS settings.
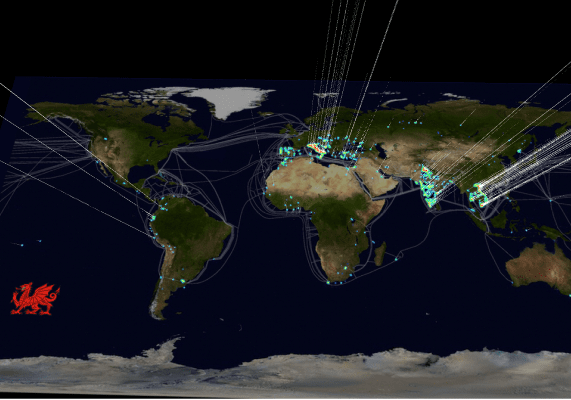
Heat map graphic of the hotspots for SOHO Pharming infections
While a similar type of attack in Poland last year was carried out to obtain online banking credentials, it is surprising to note that the people behind SOHO pharming have not yet carried out any malicious activities. Team Cymru reached out to the owners of the aforementioned IP addresses and law enforcement authorities but they haven’t obtained any reply from them.
Finally to make sure end users remain safe from this attack, Team Cymru have requested people to check the DNS settings on their routers and make sure that they match to ISP’s DNS. If they aren’t sure of their ISP’s details they can use Google DNS or OpenDNS.
Source: <a href="https://www.bbc.com/news/technology-26417441" target="_blank" rel="nofollow noopener noreferrer">Hackers take control of 300,000 home routers - BBC News</a> Image Courtesy: #-Link-Snipped-#
- In the first case, the attackers used a malicious code to target routers which had graphical user interfaces that were accessible from the Internet and then they carried out simple brute force log-on attempts to get access to the router’s configuration.
- Secondly, they targeted routers which were vulnerable to the “ROM-0†attack. The routers which ran ZyXEL’s ZynOS allowed attackers to download the configuration file from an unsecured URL. This configuration file (ROM-0) could then be used to change the DNS settings.

Heat map graphic of the hotspots for SOHO Pharming infections
While a similar type of attack in Poland last year was carried out to obtain online banking credentials, it is surprising to note that the people behind SOHO pharming have not yet carried out any malicious activities. Team Cymru reached out to the owners of the aforementioned IP addresses and law enforcement authorities but they haven’t obtained any reply from them.
Finally to make sure end users remain safe from this attack, Team Cymru have requested people to check the DNS settings on their routers and make sure that they match to ISP’s DNS. If they aren’t sure of their ISP’s details they can use Google DNS or OpenDNS.
Source: <a href="https://www.bbc.com/news/technology-26417441" target="_blank" rel="nofollow noopener noreferrer">Hackers take control of 300,000 home routers - BBC News</a> Image Courtesy: #-Link-Snipped-#
0
