Microsoft Disrupts Operations Of ZeroAccess Botnet
Microsoft’s Digital Crimes Unit has managed to disrupt operations of ZeroAccess botnet by blocking incoming and outgoing communications between computers located in the US to 18 IP addresses which were being used to carry out various malicious activities for the malware. The ZeroAccess botnet which initially went by the name Sirefef has been known to affect over two million computers worldwide. The botnet’s primary purpose is to highjack search results and lead users to unwanted sites. The purpose of redirecting users to these websites is to generate ad clicks. Various companies pay advertising revenue to websites based on the number of clicks they receive on advertisements. So this click fraud meant the cybercriminals could demand more money from advertisers depending on the number of clicks.
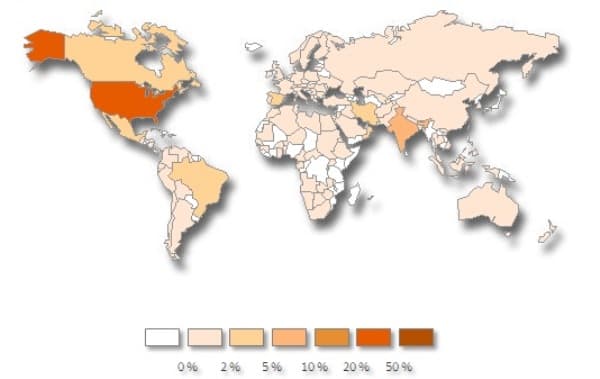
Geographic distribution of ZeroAccess botnet. Image Source: Symantec
#-Link-Snipped-# that the botnet manages to scam advertisers out of 2.7 million dollars each month by hijacking Google, Bing and Yahoo search results. The operation was carried out by collaborative efforts from Microsoft, Europol’s European Cybercrime Centre, the Federal Bureau of Investigation and A10 Networks Inc. Microsoft has also managed to take control over 49 domains associated with the ZeroAccess botnet. The threat of the botnet still looms large because it users peer-to-peer infrastructure which means that botnet can be controlled from thousands of computers by cybercriminals. In the past #-Link-Snipped-# had tried to <a href="https://www.bbc.co.uk/news/technology-24348395" target="_blank" rel="nofollow noopener noreferrer">Symantec disables 500,000 botnet-infected computers - BBC News</a> by disabling 500,000 botnet-infected computers but was not able to completely eliminate the botnet due to its decentralised nature.
Source: <a href="https://www.bbc.co.uk/news/technology-25227592" target="_blank" rel="nofollow noopener noreferrer">Microsoft disrupts ZeroAccess web fraud botnet - BBC News</a>

Geographic distribution of ZeroAccess botnet. Image Source: Symantec
#-Link-Snipped-# that the botnet manages to scam advertisers out of 2.7 million dollars each month by hijacking Google, Bing and Yahoo search results. The operation was carried out by collaborative efforts from Microsoft, Europol’s European Cybercrime Centre, the Federal Bureau of Investigation and A10 Networks Inc. Microsoft has also managed to take control over 49 domains associated with the ZeroAccess botnet. The threat of the botnet still looms large because it users peer-to-peer infrastructure which means that botnet can be controlled from thousands of computers by cybercriminals. In the past #-Link-Snipped-# had tried to <a href="https://www.bbc.co.uk/news/technology-24348395" target="_blank" rel="nofollow noopener noreferrer">Symantec disables 500,000 botnet-infected computers - BBC News</a> by disabling 500,000 botnet-infected computers but was not able to completely eliminate the botnet due to its decentralised nature.
Source: <a href="https://www.bbc.co.uk/news/technology-25227592" target="_blank" rel="nofollow noopener noreferrer">Microsoft disrupts ZeroAccess web fraud botnet - BBC News</a>
0
