Custom Made Remote Access Trojans Target Professional Poker Players
Folks at the F-Secure Labs have stumbled upon a new custom made Remote Access Trojan (RAT) that was used to infect laptops of professional poker players at this year’s European Poker Tour event held in Barcelona, Spain. The threat was brought to their attention when Jens Kyllönen, a professional poker player brought his laptop to their offices when he suspected his system might have been tampered with. Kyllönen’s ordeal began when he found that his laptop had gone missing from his hotel room at the event. He first guessed that his friend might have borrowed his laptop and he went to his friend’s room to confirm his theory but when his friend denied the whole thing he rushed back to his room and found his laptop had been returned. Since Jens plays in regular as well as online poker competitions and is known to rack up 2.5 million dollars in winnings in this high stakes games he decided to go for some professional help when he found that his system was suffering from erroneous booting after the whole lost-and-found fiasco.
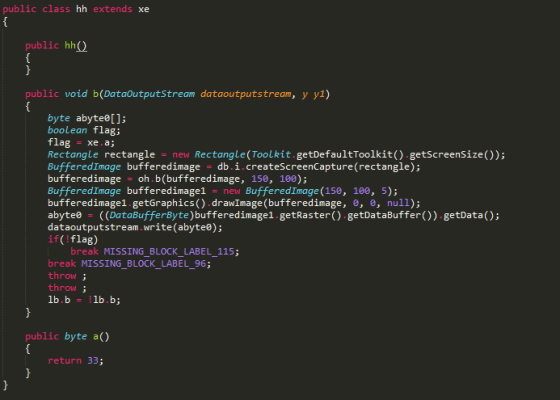
Code Snippet From The Remote Access Trojan
As soon as the team made full forensic images of the system they started going through them with a fine toothed comb. Soon they were able to find a Remote Access Trojan that had been installed in the same time frame the laptop had gone missing. The Trojan took screenshots of the victim’s screen and sent them to the attacker. Since the attacker was able to spy on the cards that Jess was holding, it gave him/her a winning edge in any online poker competition against Jens. The security analysts found this attack to be a crude one as the Trojan was installed from a USB drive (and not online) and was being hidden using simple obfuscation. The Trojan was coded in Java which meant that it could run on any platform.
Since this kind of snooping is very common now among poker players F-Secure guys have went ahead and connoted a term for these attacks.

Code Snippet From The Remote Access Trojan
As soon as the team made full forensic images of the system they started going through them with a fine toothed comb. Soon they were able to find a Remote Access Trojan that had been installed in the same time frame the laptop had gone missing. The Trojan took screenshots of the victim’s screen and sent them to the attacker. Since the attacker was able to spy on the cards that Jess was holding, it gave him/her a winning edge in any online poker competition against Jens. The security analysts found this attack to be a crude one as the Trojan was installed from a USB drive (and not online) and was being hidden using simple obfuscation. The Trojan was coded in Java which meant that it could run on any platform.
Since this kind of snooping is very common now among poker players F-Secure guys have went ahead and connoted a term for these attacks.
The phenomenon is now big enough that we think it warrants its own name: Sharking. Sharking attacks are targeted attacks against professional poker players (a.k.a. poker sharks). It's similar to Whaling attacks which are targeted at high profile business managers.Source: #-Link-Snipped-# via #-Link-Snipped-#
0
