CERT-In Warns Of Malicious 'Dendroid' RAT Affecting Android Devices In India
Computer Emergency Response Team of India (CERT-In) is yet again alerting Android smartphone users about a virus which could compromise the data stored on the phone. In its advisory, CERT-In reports a toolkit called 'Dendroid' being used to malicious applications for Android smartphones. The virus was first spotted by Symantec and in their #-Link-Snipped-# they suggest that there is a strong cybercriminal marketplace for remote access tools.

Dendroid is a HTTP Remote Administration Tool (RAT) which comes with a PHP administration panel and an application binder package. Using the Dendroid toolkit, a malicious Android application package (APK) file can be generated which will be able to offer features like the ability to delete call logs, open random webpages, record calls, intercept SMS's, change the command and control server and also perform Denial of Service (DoS) attack. Although, for cybercriminals, injecting APKs with malware isn't difficult, security researchers have still found tools similar to Dendroid which automate the process. Symantec believes that a tool known as #-Link-Snipped-# was the first malware APK binder.
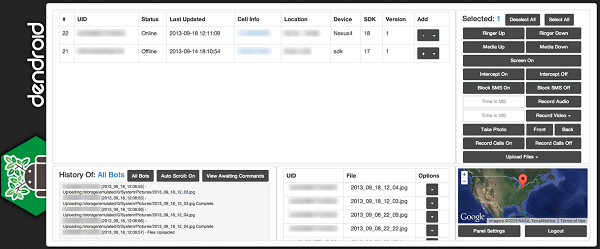
Dendroid control panel
According to a #-Link-Snipped-# in Lookout, they claim that Dendroid was designed to evade Google Play Store security. They had however detected only one application infected with Dendroid and it had already been removed from the Play Store. From underground forums, Symantec has learnt that the official seller of Dendroid is known as "Soccer" and the toolkit can be bought with a payment of $300, to be paid through BitCoin, LiteCoin or other similar services.
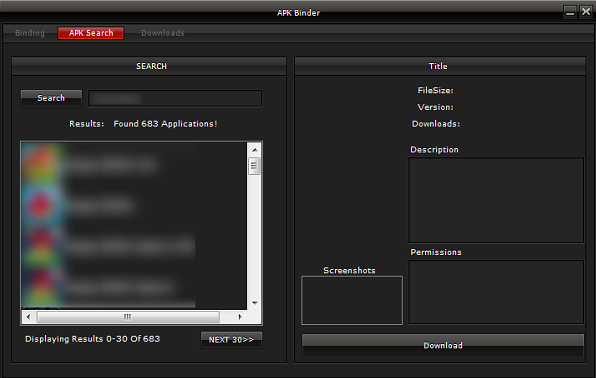
Dendroid APK Binder
CERT-In had also reported a <a href="https://www.crazyengineers.com/threads/vpn-related-security-flaw-brings-android-jellybean-and-kitkat-under-cyber-threat.73629">VPN related security flaw brings Android JellyBean and KitKat under cyber threat</a>. Android being an open source platform, has been a target for cyber criminals. To protect your phone from such attacks, it is sensible to download apps from trusted source (Google Play).

Dendroid is a HTTP Remote Administration Tool (RAT) which comes with a PHP administration panel and an application binder package. Using the Dendroid toolkit, a malicious Android application package (APK) file can be generated which will be able to offer features like the ability to delete call logs, open random webpages, record calls, intercept SMS's, change the command and control server and also perform Denial of Service (DoS) attack. Although, for cybercriminals, injecting APKs with malware isn't difficult, security researchers have still found tools similar to Dendroid which automate the process. Symantec believes that a tool known as #-Link-Snipped-# was the first malware APK binder.

Dendroid control panel
According to a #-Link-Snipped-# in Lookout, they claim that Dendroid was designed to evade Google Play Store security. They had however detected only one application infected with Dendroid and it had already been removed from the Play Store. From underground forums, Symantec has learnt that the official seller of Dendroid is known as "Soccer" and the toolkit can be bought with a payment of $300, to be paid through BitCoin, LiteCoin or other similar services.

Dendroid APK Binder
CERT-In had also reported a <a href="https://www.crazyengineers.com/threads/vpn-related-security-flaw-brings-android-jellybean-and-kitkat-under-cyber-threat.73629">VPN related security flaw brings Android JellyBean and KitKat under cyber threat</a>. Android being an open source platform, has been a target for cyber criminals. To protect your phone from such attacks, it is sensible to download apps from trusted source (Google Play).
0
