Series on Information Security -(Weekly) - Part7
Attacks
An Attack is an attempt of getting unauthorized access to computer resources bypassing the security mechanism.
There are two types of attacks,
i) Active attack
ii) Passive attack
Active attack : Here the attacker physically get access to part of the communication media and directly get in contact with the target system. Because it try to break into the target system directly, this type of attack is noisy and the target generally get alerted of the attack. Hence this is kind of attack is risky because it creates noise. Any attack that try to retrieve information directly from the target is active attack. The methods used for active attack that can be executed against the target are Ping sweep (helps to find the Live system), port scan (helps to find services running on system), DDOS (Distributed Denial Of Service attack where the services will be denied to the legitimate users of the system)etc.
Passive attack : In this case the attacker silently listens to all the communication that happens with target system. It does not attempts to get information by directly connecting to the target system. Hence this type of attack is less noisy. Sniffing is one of the best example of passive type of attack. Here generally the intention is to retrieve as much information as possible from communication that is happening between the target system and other system with whom the target is communicating. The attacker is looking for clear text communication and try to get information such as Username, password, cookies etc. Tools like tcpdump, wireshark, httpsniffer are few examples of passive attack.
One can further subdivide the type of attacks into categories according to the goal of attack. i.e. whether one want to steal , modify , impersonate as someone else or even to spoof the information for various reasons including, but not limited to monetary gains.
In this session we will cover couple of attacks and in the following session we will cover rest of them.
Man in the Middle Attack : Eavesdropping is one of the form of Man in the Middle Attack (MITM).
The attacker will maintains two separate connections between the server and the victim and relay the data on behalf of both of them. The victim never come to know that there is a third person who is listening and relaying the message. One of the method to do such type of attack is using ARP poisoning. Basically it is one of a good example of impersonation. It can be done against wired as well as wireless media. However it may be easy to get MITM executed on wireless because you don't need to be present on the physical communication medium or the actual work hall where the communication is taking place.
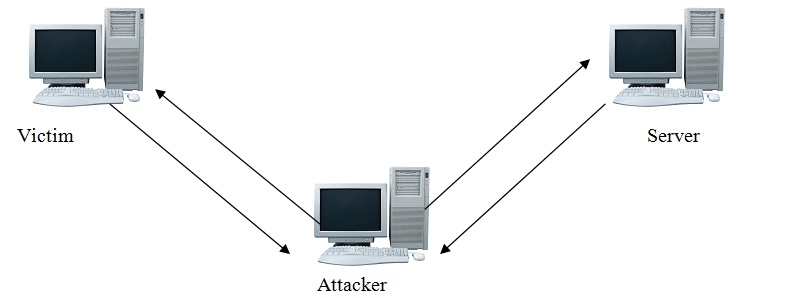
The best way to mitigate MITM attack is to encrypt data between the end points.It may protect you from the casual trace-passer but not from determined cyber criminals. One need to be extra careful and alert while carrying out crucial transactions and logins.

0

