Series on Information Security - Weekly -Part 12
Back after a long gap of 4 months. Was working on something else. But now ready for weekly details  (No breaks now) .
Last section we talked about scanning, now let dive deeper into it.
Port scanning
Best tool for this job is none other than nmap. Its also known as Swiss Knife. It provides different ways of scanning so as to avoid IDS/IPS systems. Few of the ways are ,
TCP connect  scan: They are used to complete three way tcp handshake to identify if the port is working. However this kind of scans are log-gable. The advantage of using TCP connect scan is you do not require root privileges to run it. Here more number of packets needs to be traveled and hence generates more noise and such a scan can be logged.
TCP Half-open scan: Â In this case the source would initiate the SYN packet to the destination and waiting to receive SYN-ACK or RESET packet to be received. After receiving SYN-ACK o RESET packet you tear down the connection without send ACK packet i.e. you do not complete three way TCP handshake. It is difficult to detect such type of scans. Unfortunately you needs root privileges to execute such a scan as custom tcp packet needs to be formed.
FIN Scan: Here the source would send a FIN packet to the target, if the target is not running any service on that port , it will send a RST packet to the source, this indicates that the destination is working. If the port/service is available on that host, the host will discard the TCP FIN packet and not will not respond to source indicating the service is running on the destination host.
Xmas Scan : Xmas scans have the URG, FIN and PUSH flags set.No response to a Xmas scan indicates that the port is either open or filtered. A TCP Reset response indicates the port is closed.
Let us take one nmaps example,
The Xmas tree scan output shows similar results to the FIN scan:
# nmap -sX -v 192.168.1.8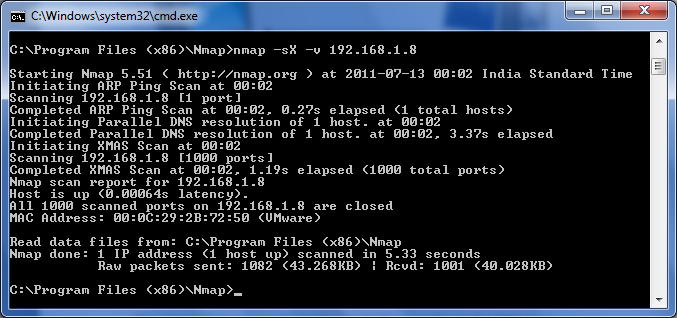
One more type of scan, I would like to mention here is,
NULL Scan : No flags are set. In real world this condition never arises. Since there are no flags set, the target will not know how to handle the request. It will discard the packet and no reply will be sent. If port is closed or no service is serving that port then the target will send RST packet. In case the port is open on the Target system, it does not know how to handle such request and hence will not respond.
#-Link-Snipped-#Â
