Software To Read Your Lips For Secure Authentication And Access - Mu'tah University
With fingerprint sensors only now entering our mobile devices, it's time for other secure authentication techniques to arrive in the latest software on our computers. Keeping up with fast pace in the security techniques development, Ahmad Hassanat from the IT Department at Mu'tah University in Jordan has come up with a software that reads the user's lips to authenticate him for logging into the computer. By making the machine learn how to analyze the pattern in lip & mouth movements, Hassanat could train the system to identify words being uttered correctly about 80% of the time.
In a paper published on this research work, Hassanat shares that the system is a two stage process - setting the visual password stage and the verification stage. By speaking the word into the camera, the system captures the video of the user's face and a words-based VSR system processes these words to extract a sequence of feature vectors. Later, when the user is trying to log-in, these features are compared with the stored visual password and the access is granted.
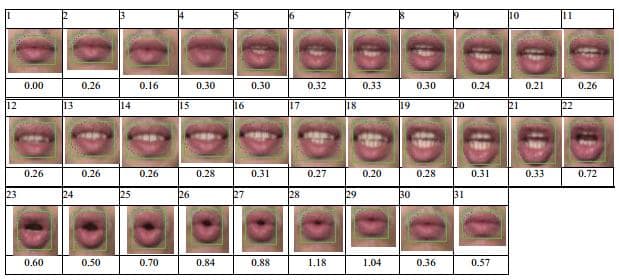
The appearance of mouth when uttering the word 'Zero'.
Ahmad Hassanat evaluated his system with a video database of 10 males and 10 females and found that system's feasibility is great and has the potential for practical approach thanks to error rate in the range of 7.63% to 20.51% at the worst tested scenario. The author of the paper claims that this new form of visual password would be the newest way for biometric security as even the best of actors would not be able to exactly mimic someone else's lip movements.
What would be the disadvantages of such a system? Let us know your thoughts in comments.
Source: International Journals: Publishing Research Papers in all Fields
In a paper published on this research work, Hassanat shares that the system is a two stage process - setting the visual password stage and the verification stage. By speaking the word into the camera, the system captures the video of the user's face and a words-based VSR system processes these words to extract a sequence of feature vectors. Later, when the user is trying to log-in, these features are compared with the stored visual password and the access is granted.

The appearance of mouth when uttering the word 'Zero'.
Ahmad Hassanat evaluated his system with a video database of 10 males and 10 females and found that system's feasibility is great and has the potential for practical approach thanks to error rate in the range of 7.63% to 20.51% at the worst tested scenario. The author of the paper claims that this new form of visual password would be the newest way for biometric security as even the best of actors would not be able to exactly mimic someone else's lip movements.
What would be the disadvantages of such a system? Let us know your thoughts in comments.
Source: International Journals: Publishing Research Papers in all Fields
Replies
-
 Rajni JainAwesome !
Rajni JainAwesome !
However, I am all puzzled if uttering the password would be a safe and secure way of authentication? Also, one can utter the password with different lip movement, how would software recognize that.
Meanwhile, it is a good start for another way of authentication. -
 Ankita Katdare#-Link-Snipped-# Yeah, doesn't look full-proof. It seems that any kind of movement (be it fluttering of eye-lids) that is unique to every individual and form a pattern is being tested for secure authentication mechanisms.
Ankita Katdare#-Link-Snipped-# Yeah, doesn't look full-proof. It seems that any kind of movement (be it fluttering of eye-lids) that is unique to every individual and form a pattern is being tested for secure authentication mechanisms. -
 Mvrajokay its good but others can easily hack that what she/he utter some words at that time so how well is your software please tell me madam?
Mvrajokay its good but others can easily hack that what she/he utter some words at that time so how well is your software please tell me madam? -
 Suraj PatilGreat! Now we'll speak our passwords, I guess hackers won't need keyloggers anymore.
Suraj PatilGreat! Now we'll speak our passwords, I guess hackers won't need keyloggers anymore.
Research should be focused on making good solutions to real problems, it shouldn't be to create another problem.
It is a good idea, wrong implementation.
May be lip reading can be used to give commands to your cellphone just like voice activated commands. -
 hitoshianatomiWhether static or behavioral or electromagnetic, biometrics cannot be claimed to be an alternative to passwords UNTIL it stops relying on a password for self-rescue against the false rejection altogether while retaining the near-zero false acceptance in the real outdoor environment. A dog which depends on a man cannot be an alternative to the man.
hitoshianatomiWhether static or behavioral or electromagnetic, biometrics cannot be claimed to be an alternative to passwords UNTIL it stops relying on a password for self-rescue against the false rejection altogether while retaining the near-zero false acceptance in the real outdoor environment. A dog which depends on a man cannot be an alternative to the man.
Biometrics can theoretically be operated together with passwords in two ways, (1) by AND/conjunction or (2) by OR/disjunction. I would appreciate to hear if someone knows of a biometric product operated by (1). The users of such products must have been notified that, when falsely rejected by the biometric sensor with the devices finally locked, they would have to see the device reset. It is the same with the biometrics operated without passwords altogether.
Biometric products are generally operated by (2) so that users can unlock the devices by passwords when falsely rejected by the biometric sensors. This means that the overall vulnerability of the product is the sum of the vulnerability of biometrics (x) and that of a password (y). The sum (x + y - xy) is necessarily larger than the vulnerability of a password (y), say, the devices with biometric sensors are less secure than the devices protected only by a password.
It is very worrying to see so many ICT people being indifferent to the difference between AND/conjunction and OR/disjunction when talking about “using two factors together”.
You are reading an archived discussion.
Related Posts
I'm trying to purchase a tripod and constantly getting Failed to login, please retry after some time error whenever I try to login - on the modal window as well...
Handa Ka Funda is an online platform for CAT preparation founded by Ravi Handa in the year 2013. Ravi Handa teaches Quantitative Aptitude, Logical Reasoning and Data Interpretation to thousands...
when did the online application starts
Intex Technologies has launched a new smartphone known as 'Intex Aqua Y2 Pro' that is priced below Rs. 5,000 and offers a 1 GHz MediaTek (MT6572) Dual Core processor running...
Both landline and mobile calls made within India will be banned by Skype starting November 10. The reasons for this move have not been published by Microsoft (Skype's owner) yet....
