Notorious Botnet Simda Taken Down By Authorities
Law enforcement and cyber firms across the world joined hands to take down a notorious botnet that had managed to infect 770,000 computers across the world. The botnet titled Simda had first surfaced in 2012 and was manipulating of internet traffic and spreading other malware to systems. Even though Simda managed to affect 128,000 new computers every month it managed to elude security experts because every time they tried to study the malware in a sandbox environment it tricked them by not functioning properly or by sleeping indefinitely. It also informed the owner of the botnet about the IP address of the researchers’ systems so that he/she avoids those IP addresses the next time. Just like Beebone, Simda too relied on polymorphism but on the server side.
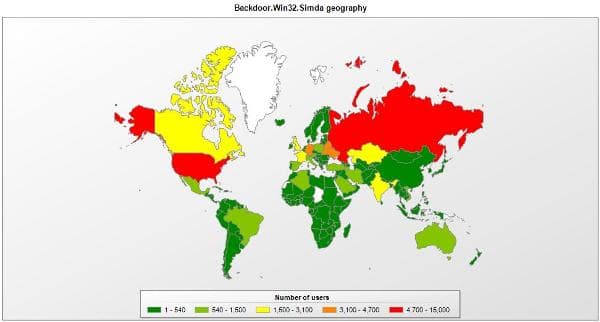
Affected Users Across The World
Simda managed to infiltrate systems by finding known exploits in software like Silverlight, Java and Adobe Flash, through mass SQL injection, by using exploit kits such as Blackhole, Styx, Magnitude and Fiesta, spam mail and social engineering. Once it got into a system it kept the botnet owner informed about its activities. It changed the hosts file in SYSTEM32 to redirect internet traffic and once that was over, it used to exit from the system. Simda also manipulated the victims communication to websites like connect[dot]facebook[dot]net and Google analytics.
Simda was brought down by the same sinkholing procedure that was used to takedown Polymorphic Botnet Beebone Brought Down By US and European Authorities. The authorities managed to identify and shutdown 14 command and control centres in Netherlands, USA, Luxembourg, Poland and Russia. Agencies such as Microsoft, TrendMicro, Kaspersky Labs, Cyber Defense Institute, Dutch National High Tech Crime Unit, FBI and Luxemburg and Russian police worked under the supervision of Interpol to bring down the botnet. They have secured the server logs of the botnet and currently have the list of all the people who were infected by the malware. If you have been infected your ISP shall inform you about in the coming days or you can visit a #-Link-Snipped-# that tells you if you are among those victims or not.
To know more about Simda you can read reports from #-Link-Snipped-#, #-Link-Snipped-#, #-Link-Snipped-# and its coverage on #-Link-Snipped-#.

Affected Users Across The World
Simda managed to infiltrate systems by finding known exploits in software like Silverlight, Java and Adobe Flash, through mass SQL injection, by using exploit kits such as Blackhole, Styx, Magnitude and Fiesta, spam mail and social engineering. Once it got into a system it kept the botnet owner informed about its activities. It changed the hosts file in SYSTEM32 to redirect internet traffic and once that was over, it used to exit from the system. Simda also manipulated the victims communication to websites like connect[dot]facebook[dot]net and Google analytics.
Simda was brought down by the same sinkholing procedure that was used to takedown Polymorphic Botnet Beebone Brought Down By US and European Authorities. The authorities managed to identify and shutdown 14 command and control centres in Netherlands, USA, Luxembourg, Poland and Russia. Agencies such as Microsoft, TrendMicro, Kaspersky Labs, Cyber Defense Institute, Dutch National High Tech Crime Unit, FBI and Luxemburg and Russian police worked under the supervision of Interpol to bring down the botnet. They have secured the server logs of the botnet and currently have the list of all the people who were infected by the malware. If you have been infected your ISP shall inform you about in the coming days or you can visit a #-Link-Snipped-# that tells you if you are among those victims or not.
To know more about Simda you can read reports from #-Link-Snipped-#, #-Link-Snipped-#, #-Link-Snipped-# and its coverage on #-Link-Snipped-#.
Replies
You are reading an archived discussion.
Related Posts
There are moments in life when you do want to go back in time just to alter something!
Well I have literally watched all the videos that I could locate...
Hi Everyone,
I see so many posts here by fresh engg. graduates about software testing vs development career career related questions.
This post is just about my perspective of both...
Google Inc. has launched a new Handwriting Input app on Google Play store. As the name suggests, it lets you enter text using your own handwriting. What's so impressive about...
Quote: Robots have already revolutionized medical device manufacturing [3], but now they're coming out of the factory and into the clinic.
Valued at $1.8 billion in 2013, the market for...
You may now Google 'Find My Phone' and let the search engine show the location of your phone on a map. If you are habitual phone forgetter, you may have...
